Secure Java Programming
1 Java Security
- https://www.google.com/search?q=java+vulnerabilities+2013
- The Java Language Environment The Byte Code Verification Process:
Checks class files before running.
- Jumps (Branches) are always to locations within the same method.
- Data is always initialized and references are always type-safe.
- Access to private data and methods is controlled.
- http://docs.oracle.com/javase/specs/jvms/se7/html/jvms-4.html#jvms-4.10
- Sandbox: Local code is trusted to have full access to local resources (such
as the file system) while (downloaded) remote code (e.g., an
applet) is not trusted and can access only the limited resources
provided inside the sandbox. The sandbox is a set of rules.
Similar to
chroot"jail". - .
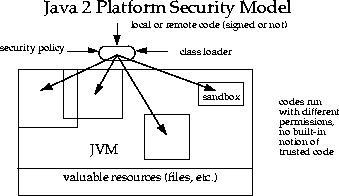 Java Sandbox
Java Sandbox
2 Java Classloaders
java.lang.ClassLoaderPart of the JRE that dynamically load classes into the JVM.- Environments are populated from the system (boot) classpath, app server classpaths, application classpaths, and many more.
- Applet Class Loader – when and how an applet can add/replace classes to JRE. Applets are sent by a web server.
- The bootstrap class loader loads the core libraries
$JAVA_HOME/jre/lib - The extensions class loader loads the code in the extensions
directories
$JAVA_HOME/jre/lib/ext - The system class loader loads code found on
$CLASSPATH. - Classes loaded by different loaders do not have package-private access to one another even if they have the same package name.
- http://www.onjava.com/pub/a/onjava/2005/01/26/classloading.html Reference
- The hierarchies of class loaders are increasingly complex, as are the environments they produce. http://incubator.apache.org/depot/version/jar-hell.html Reference
3 The Security Manager
SecurityManager appsm = System.getSecurityManager();- Defines a security policy for an application.
- system policy file
${JAVA_HOME}/lib/security/java.policy - Applies to all Java programs that run in the JVM on that system
grant signedBy "Duke" { permission java.io.FilePermission "/tmp/*", "read,write"; }; // Grant everyone the following permission: grant { permission java.util.PropertyPermission "java.vendor", "read"; };
- Java library checks with SM whenever a "dangerous" operation is about to be called.
- SM can raise a
SecurityExceptionjava.security.AccessControlException: access denied (java.io.FilePermission some-file-name read)
grant codeBase "file:user_client_installed_location" { permission java.io.FilePermission "that-file-name", "read"; };
4 JAR file Manifest Attributes
- The Permissions attribute is used to ensure that the application requests only the level of permissions that is specified in the applet tag or JNLP file.
- The Codebase attribute is used to ensure that the code base of the JAR is restricted to specific domains.
- The Application-Name attribute is used to provide the title that is shown in the security prompts for signed applications.
- The Application-Library-Allowable-Codebase attribute is used to identify the locations where your application is expected to be found.
- The Caller-Allowable-Codebase attribute is used to identify the domains from which JavaScript code can make calls to your application.
- The Trusted-Only attribute is used to prevent untrusted components from being loaded.
- The Trusted-Library attribute is used to allow calls between privileged Java code and sandbox Java code without prompting the user for permission.
5 References
- http://docs.oracle.com/javase/tutorial/index.html Java Tutorials by sun/oracle.com. Excellent tutorials. Free to download in its 1000+ page entirety. Recommended Reading.
- http://docs.oracle.com/javase/tutorial/security/index.html "Tutorial Trail: Security Features in Java SE" From the above. Highly Recommended Reading.
- http://www.oracle.com/technetwork/java/seccodeguide-139067.html Secure Coding Guidelines for Java. CS7140 version ./sec-java-oracle-pm-edited.html Required Reading.
- Java Security Resource Center http://www.oracle.com/technetwork/java/javase/overview/security-2043272.html Reference